1. Introduction: The Illusion of Security
IBAN-name checks have become a standard step in corporate payment processes—offering a quick way to confirm that the beneficiary name matches the bank account details. Mandated across many European markets, this control helps prevent misdirected payments caused by human error or miscommunication.
But while IBAN-name matching reduces friction, it doesn't eliminate fraud.
Vendor impersonation, fake onboarding, and compromised supplier records are now among the most common forms of B2B fraud. In these scenarios, the IBAN may match the name—but the company behind it may be dissolved, fraudulent, or untraceable. Without validating the existence, status, and ownership of the vendor, organizations remain vulnerable—even with IBAN-name checks in place.
This is why leading finance and procurement teams are rethinking vendor authentication altogether. They're moving beyond surface-level checks and adopting real-time, registry-based verification powered by API integrations.
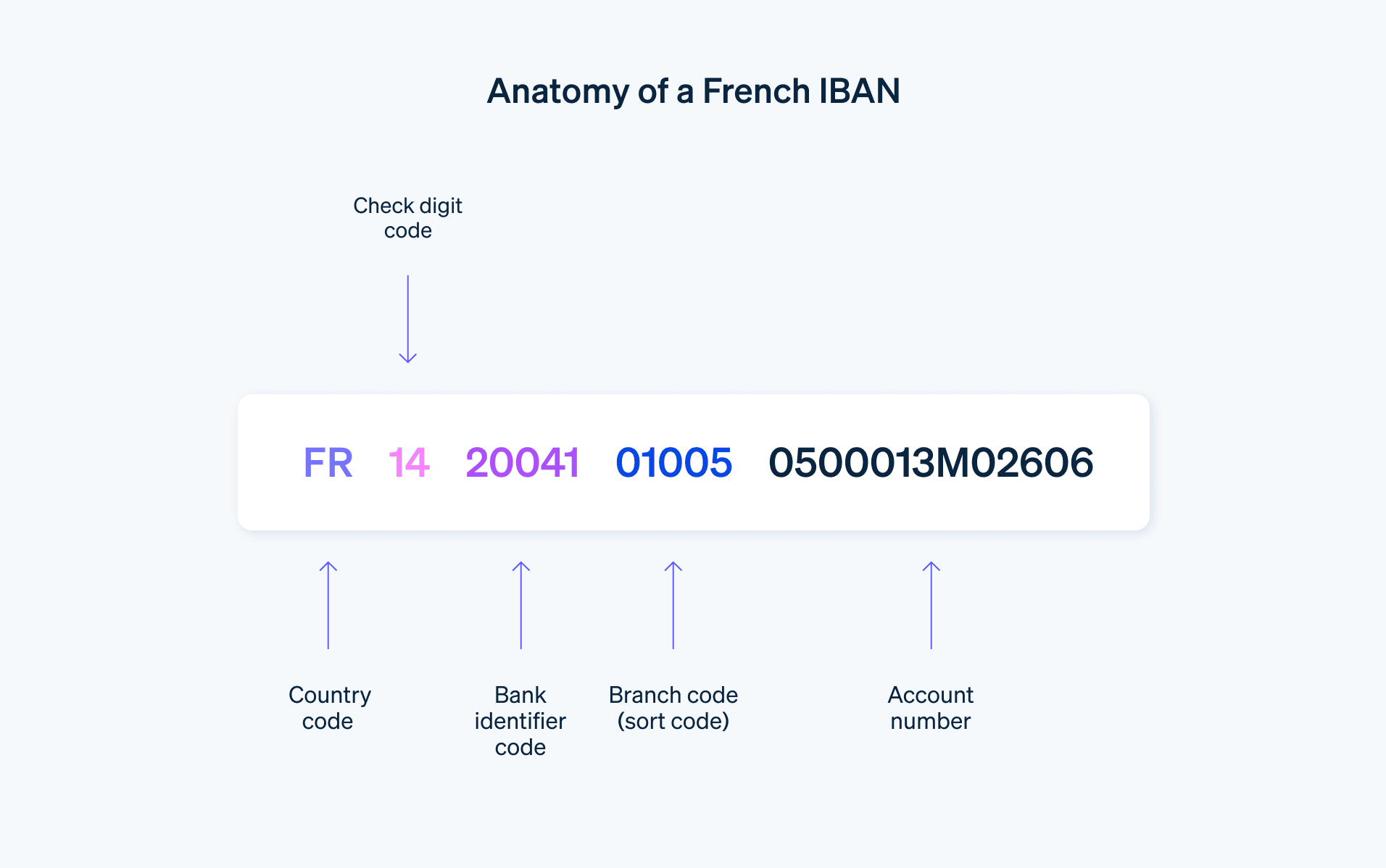
What Is an IBAN?
An IBAN (International Bank Account Number) is a standardized international format used to identify bank accounts across borders. It was developed to streamline cross-border payments within Europe and globally by reducing errors and ensuring consistency in account identification.
An IBAN typically includes:
- A country code (e.g., NL for the Netherlands, DE for Germany)
- A two-digit check number
- A bank identifier
- A domestic account number
For example, an IBAN in the Netherlands might look like: NL91ABNA0417164300.
While the IBAN helps route payments to the correct bank account, it does not by itself confirm the identity of the account holder. That’s where additional controls like IBAN-name matching and, more importantly, company-level verification come into play—especially in B2B transactions where the risk of fraud is significantly higher.
2. What IBAN-Name Checks Do Well (and Where They Fall Short)
As IBAN became the global standard for identifying bank accounts, financial institutions and regulators introduced a complementary safeguard: the IBAN-name check, also known as Confirmation of Payee (CoP) in the UK and parts of Europe.
How IBAN-Name Checks Work
Before executing a payment, the system compares the name of the intended beneficiary with the name registered to the IBAN. If the names match, the transaction proceeds. If there’s a discrepancy, the sender is alerted—giving them the chance to double-check with the recipient before sending funds.
It’s a simple and effective way to prevent:
- Fat-finger errors when entering IBANs manually
- Mistaken payments due to similar vendor names
- Common misrouting in supplier onboarding
Where IBAN-Name Checks Fall Short
Despite their value, IBAN-name checks are not designed to detect fraud. They answer only one question: Does the name match the IBAN? But they don’t address deeper—and far more critical—risks, such as:
- Does this company actually exist?
- Is it legally registered and active?
- Is the person or entity requesting payment authorized?
- Has the bank account changed recently, possibly due to a compromise?
Moreover, IBAN-name checks are typically limited to domestic banking networks and depend heavily on the quality and completeness of the bank’s data. They do not validate the underlying business entity behind the account.
This creates dangerous blind spots—particularly in high-value B2B transactions, onboarding new suppliers, or working with companies in unfamiliar jurisdictions.
3. The Growing Sophistication of Vendor Fraud
Vendor fraud has evolved far beyond fake invoices and internal collusion. Today’s fraudsters use highly targeted, well-orchestrated attacks that bypass traditional controls—including IBAN-name checks. As payment processes become more automated, so do the threats.
Common Tactics Used by Fraudsters
- Fake Suppliers: Fraudsters create entirely fictitious vendors, complete with forged documents, plausible business names, and seemingly legitimate bank details. Once onboarded, they receive payments with little scrutiny.
- Vendor Impersonation: A real supplier’s identity is hijacked—often via email spoofing or hacked systems—and bank account details are quietly replaced during a routine update.
- Lookalike Entities: Fraudsters register companies with nearly identical names to legitimate suppliers in a different jurisdiction. They then issue invoices that appear valid, but redirect funds to controlled accounts.
- Social Engineering: Attackers impersonate procurement staff, CFOs, or vendors themselves—convincing finance teams to override standard controls "urgently."
Why IBAN Checks Can’t Keep Up
In each of these cases, the IBAN may be valid and match the name provided, but the account itself is unauthorized, fraudulent, or misused. Without validating the legal status of the entity, its registration, and ownership structure, organizations are often unaware they’ve been compromised—until the money is gone.
And with fraud attempts becoming cross-border, multi-layered, and time-sensitive, relying on static checks or outdated records is a critical weakness.
4. Beyond IBAN Checks: What True Vendor Authentication Looks Like
To effectively prevent fraud in B2B transactions, companies must shift from surface-level controls to deep, data-driven verification of vendors. This means moving beyond just checking whether a bank account exists, and instead validating whether the company itself is legitimate, active, and authorized to receive payment.
✅ Key Elements of True Vendor Authentication:
1. Verify Legal Entity Existence
Confirm that the company is officially registered with the local government registry. This includes retrieving its legal name, company number, VAT number, and jurisdiction of incorporation.
2. Check Company Status
Determine whether the entity is active, dormant, dissolved, or under liquidation. This avoids onboarding or paying companies that no longer legally operate.
3. Validate Incorporation Date
A newly registered company posing as a long-standing vendor is a red flag. The incorporation date provides important context and helps identify shell companies or fraudulent setups.
4. Confirm Registered Address
Ensure the supplier's address is consistent with its legal records. Mismatches here can be a sign of impersonation or deliberate obfuscation.
5. Review Shareholder & UBO Data
Know who ultimately owns or controls the company. Identifying Ultimate Beneficial Owners (UBOs) is critical for compliance, sanctions screening, and fraud prevention.
6. Match Bank Details to Verified Entity
The bank account being used should match the verified company’s legal profile. If a supplier’s account is registered under a different name or a dissolved entity, it may indicate fraud or account hijacking.
7. Enable Ongoing Monitoring
Fraud doesn’t stop after onboarding. Monitor vendors continuously for changes to bank accounts, ownership, legal status, or contact details—triggering alerts when anomalies arise.
This level of vendor authentication can’t be done manually or through outdated spreadsheets. It requires access to real-time, authoritative data—preferably pulled directly from government sources and standardized across borders.
That’s where Global Database comes in.
5. Why the Source of Data Matters
When it comes to verifying vendors, the strength of your decisions depends entirely on the quality and credibility of the data behind them. Many organizations rely on internal spreadsheets, third-party databases, or outdated public listings. While these may offer convenience, they come with serious limitations—and dangerous blind spots.
❌ The Problem with Weak Data Sources
- Outdated Records: Static databases are often months or years behind real-time changes like company dissolution, change of ownership, or newly created entities.
- Unverified Inputs: Data scraped from the web or contributed by users is difficult to audit and prone to manipulation.
- Lack of Global Coverage: Most data providers have patchy international reach, making it hard to verify cross-border vendors.
- Inconsistent Formats: Local registry data is often unstructured, multilingual, and fragmented—difficult to standardize without dedicated infrastructure.
✅ Why Registry-Sourced Data Is the Gold Standard
Government business registries are the only authoritative source for validating whether a company legally exists, is active, and is operating under proper ownership. These registries capture:
- Legal entity names
- Registration numbers
- Incorporation dates
- Status (active, dissolved, bankrupt)
- Registered addresses
- Legal representatives, shareholders, and UBOs (in many jurisdictions)
But accessing and normalizing this data across more than 100 countries is a technical and logistical challenge. That’s where the Global Database API delivers strategic value.
🔗 How Global Database Bridges the Gap
- First-Party Data: Global Database sources directly from official government registries—no scraping, no estimation.
- Global Reach: Coverage across 100+ countries, including Europe, North America, LATAM, APAC, and offshore jurisdictions.
- Unified Format: All data is cleaned, structured, and normalized—so you don’t have to deal with different formats per country.
- Real-Time Delivery: Data is accessible via API in real time, ensuring that decisions are based on up-to-date, verified information.
In vendor authentication, the source isn’t just a detail—it’s the difference between confidence and exposure.
6. Inside the Global Database API: Verified Data from 100+ Registries
The Global Database API is built to power real-time vendor authentication at scale—by connecting directly to official government registries in over 100 countries. It gives finance, compliance, and procurement teams a single, unified interface to verify suppliers and mitigate fraud across any jurisdiction.
🌍 What You Can Search By
The API supports multiple search methods depending on the data available:
- Company Registration Number (preferred for precision)
- VAT Number
- Company Name + Address (used when IDs are unavailable or incomplete)
This flexibility allows users to query confidently, even with partial vendor data—ideal for onboarding workflows and third-party risk systems.
📦 What the API Returns
Global Database returns a standardized company profile that includes:
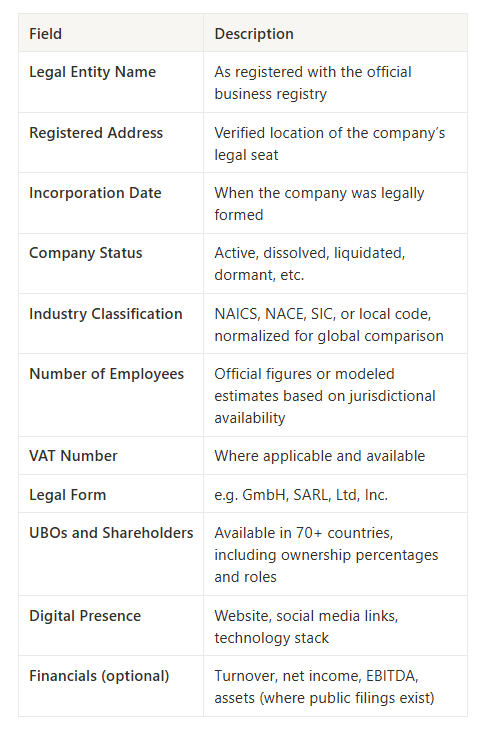
By embedding registry-sourced verification directly into the vendor lifecycle, organizations can automate trust at every stage—from onboarding to payment—and stay ahead of fraud without adding operational overhead.
7. The Power of Global Coverage in Fraud Prevention
Vendor fraud isn’t limited to domestic suppliers—and your verification strategy shouldn’t be either. As businesses expand globally, procurement and finance teams routinely work with vendors in unfamiliar jurisdictions, each with its own rules, documentation standards, and risk landscape.
This is where global registry coverage becomes critical.
🌐 Fraud Is Global—Your Verification Must Be Too
- A vendor incorporated last month in Cyprus may appear legitimate in a surface-level check.
- A dissolved supplier in Brazil could still be listed in your ERP with no alert.
- A payment to a bank account in Singapore may look correct—even if the company was never officially registered.
Without access to up-to-date registry data from each local authority, these risks go undetected.
✅ How Global Database Solves This
With verified data from over 100 official registries, Global Database enables companies to:
- Verify suppliers anywhere in the world—whether in the EU, US, LATAM, APAC, or offshore zones
- Normalize and compare vendor profiles across countries, using unified legal form, industry code, and status fields
- Maintain a single validation workflow across geographies—no need to build custom logic for each country
- Stay audit-ready, backed by verifiable government-sourced documentation
🛡️ Coverage Enables Control
Global coverage doesn’t just reduce fraud—it ensures:
- Better onboarding accuracy
- Faster vendor approvals
- Stronger compliance with AML, sanctions, and tax regulations
- Fewer manual escalations or false positives
In short, without global reach, vendor authentication remains fragmented—and vulnerable.
8. Use Case: Real-Time Vendor Validation Before Every Payment
Let’s walk through how leading companies are embedding real-time vendor authentication into their procurement and finance workflows using the Global Database API.
🔄 Typical Workflow: Pre-Payment Vendor Check
Step 1: Trigger
A vendor is added or updated in the ERP or P2P system (e.g. SAP, Coupa, Oracle). This could be during onboarding, master data updates, or before a scheduled payment.
Step 2: API Call
The system sends a request to Global Database’s API using:
- Registration number
- VAT number
- Or company name + address
Step 3: Verification
The API returns a real-time company profile, pulled from official registries. Key fields like legal name, address, incorporation date, and company status are checked against the vendor master record.
Step 4: Decision Logic
- ✅ If the data matches and the company is active → Payment approved
- ⚠️ If mismatches are detected (e.g. wrong name, dissolved status, unregistered entity) → Payment flagged or paused
- 🔁 Optional: Trigger additional checks (e.g. UBO review, sanctions screening)
Step 5: Logging & Audit
The response is logged for compliance purposes, providing a verifiable record that the company was validated against government sources at the time of payment.
📈 Benefits Realized
- Reduces fraud exposure by validating both the bank account and the legal entity
- Shortens onboarding time with real-time results
- Supports regulatory compliance (e.g. AML, KYC/KYB, FATF guidelines)
- Scales globally without creating separate processes for each country
- Strengthens data quality in ERP and procurement systems
Whether you're onboarding a supplier in Germany, verifying a distributor in Singapore, or reviewing a change request in the US, real-time registry data ensures you’re not flying blind. You’re verifying facts—not assumptions.
9. Conclusion: IBAN Checks Are a Start—But Not a Solution
IBAN-name checks have become a foundational control for preventing simple payment errors—but they were never designed to stop fraud. As vendor fraud becomes more sophisticated, finance and procurement teams need to go deeper. Surface-level checks can’t tell you if a company actually exists, if it’s active, who owns it, or if the bank account has been quietly updated by someone with malicious intent.
To truly secure B2B transactions, vendor authentication must be built on authoritative, real-time data—not guesswork or outdated records.
This is where solutions like the Global Database API provide a critical advantage. By connecting directly to over 100 official registries worldwide, it gives companies the ability to:
- Validate suppliers before onboarding
- Verify company legitimacy before every payment
- Monitor vendor data over time
- Automate controls at global scale
The result?
- Fewer fraud attempts reaching the payment stage
- Faster, safer approvals
- Audit-proof compliance with evolving regulations
In today’s risk landscape, IBAN-name checks are a helpful step.
But if you’re serious about preventing fraud, you need to know more than just the name behind the bank account—you need to know the entity behind the invoice.
